Identity Bridge
Bridge Different Digital Identities for the Modern Financial Ecosystem
Identity management is a complex task for businesses, and one that very often deals with legacy systems working with different data formats. Knox has simplified this approach by utilizing a standards-based identity bridge, which can safely and securely provide a lingua franca for all ID systems.
Knox Networks' Digital Identity Bridge was created to solve the following problems within industry:
- Identity systems are incompatible with PKI-based payment networks and compliance/screening
- Participant Banks have different identity systems - Hard to onboard and extend services
- Bank Transactions involve sharing significant amounts of PII/commercially sensitive information.
To solve these problems, Knox has created a solution that can:
- Bridge any existing systems to W3C standard Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs)
- Interoperate with standardized IDs and cryptographic credentials for harmonized verification and onboarding
- Protect sensitive data with verification and compliance checks via privacy-enhancing technologies (PETs)
Identity Bridge & Wallet SDK
- Keep existing systems and KYC, add on bridge microservices
- Privacy & Security - Data held & controlled in user wallet enclave, cryptographically shared only as required
- Standards-based interoperability among all networks
Standards-Based Identity
W3C Decentralized Identifiers (DID) - https://www.w3.org/TR/did-core/
- Identify user wallets by Public Key Infrastructure (PKI) based cryptography
- No sensitive data stored, vendor-agnostic
W3C Verifiable Credentials (VC) - https://www.w3.org/TR/vc-data-model/
- Digital form of physical credentials (e.g. Bank Account, Accredited Investor Profile)
- Contains cryptographic proofs, has tamper resistance through digital signatures/hashes
- Zero Knowledge Proofs- >18 instead of Birthdate, >200K without exposing income
Privacy-Enhancing Techniques (PETs)
Knox can support a variety of different Privacy-Enhancing Techniques (PETs) in the system, including:
- Zero-Knowledge Proofs
- Homomorphic Encryption
- Confidential Screening (shown below)
- and others
Knox Digital Identity Benefits
- Security and Privacy First: Contains security features to ensure that the data is protected and accessible only by those with the appropriate authority
- Enables new modes of privacy-preserving identity that allows many forms of credentials to be concurrently issued and allows for efficient verification
- Provides a trusted solution to manage private keys and the exchange of credentials
- Allows the use of Hardware security modules (HSMs) to enable password-less access
- Ease of Use: Built to enable easy use across an enterprise environment
- Ability to use digital certificates to authenticate and sign transactions, documents, and messages
- Eliminates the need for custom tokens as identity is managed in mobile and custodial wallets that use secure enclaves
- Capture Critical Information: Provides the ability to run regulatory compliant programs, including onboarding, “Know Your Customer” (KYC), and other Anti-Money Laundering (AML) services program
- Flexible: Enables straightforward and efficient implementations even though every enterprise has different requirements depending on the use case and applicable regulatory regime.
- The system can accommodate different levels of identification. It can be configured to allow users to provide certain information necessary for a particular transaction (e.g., more details for a larger transaction, including enhanced due diligence information)
- Access rights, privacy management and other key features are set by the enterprise based on their own requirements
- Traceable: Easy auditing of transactions, including storing pseudonymous information in the history of each transaction.
Walkthrough: Linking an Institution's Existing Users to DIDs and VCs

Sample Digital ID Verification Process
Project Integration:
- Knox Service integrates against the existing Institution A identity system over OIDC/SAML, or other existing APIs.
- Knox provides infra & deployment scripts to have its services installed in the institution network.
First Time User Login- INITIAL SETUP ONLY:
- User is a customer of Institution A and logs in using existing bank login credentials, proxied through Knox Services
- Knox Service creates a user wallet, its Decentralized Identifier (DID), and its DID Document pushed to the registry
- The wallet is linked to the logged-in user, and a Verifiable Credential (VC) is issued to store the user's account details.
- The user now has the Institution A VC with its information. This data can be shared going forward by the user for verification and can obtain more VCs (e.g., Accredited Investor VC)
Walkthrough - Confidential Screening against Counterparty Data and Policy
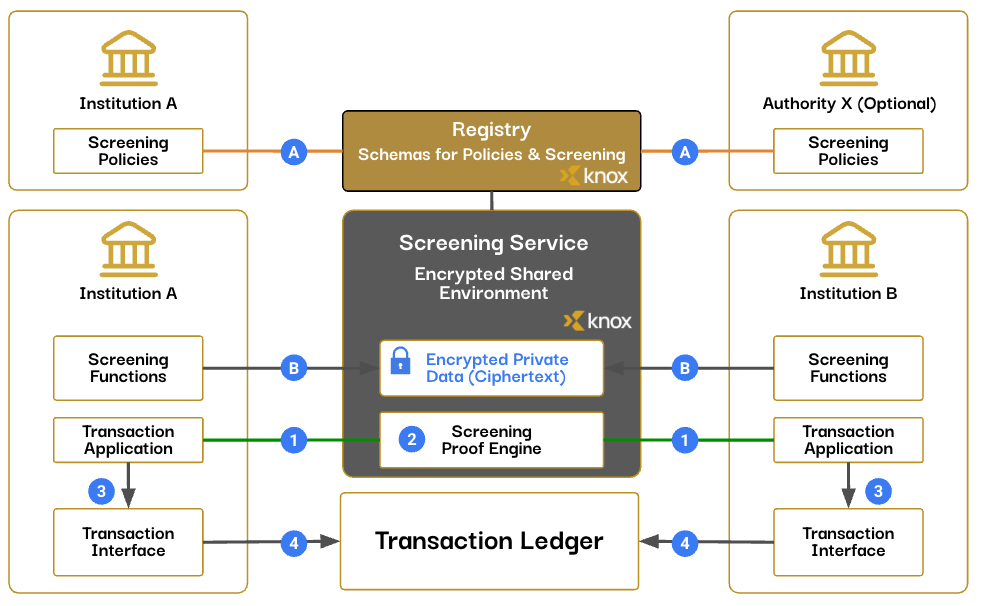
Sample Confidential Screening
Pre-Transaction:
A. Authorities sets screening policies and requirements.
B. Institutions load their client data in encrypted ciphertext. (e.g. Accredited Investor/QIBs Profile, Sanctions)
Transaction:
- Screening function in Institution A issues encrypted search of its sender on the Institution B lists
- Screening Engine generates proof that the sender passed receiver Accredited Investor check (or Sanctions)
- Screening proof is attached with payment message
- Institution B can repeat the screen of the sender ciphertext with high assurance of passing, before accepting transfer
Updated 5 months ago
What’s Next
